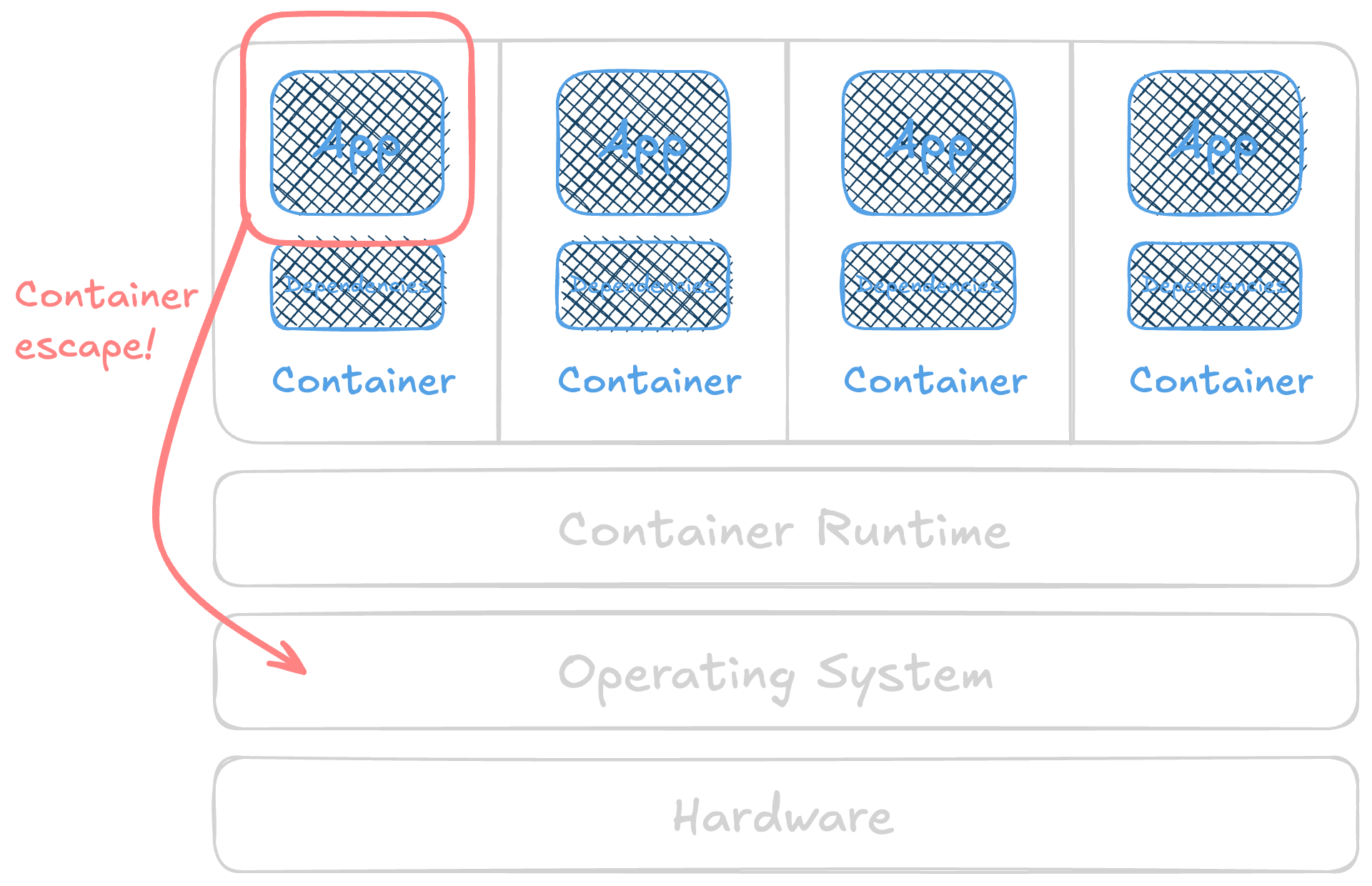
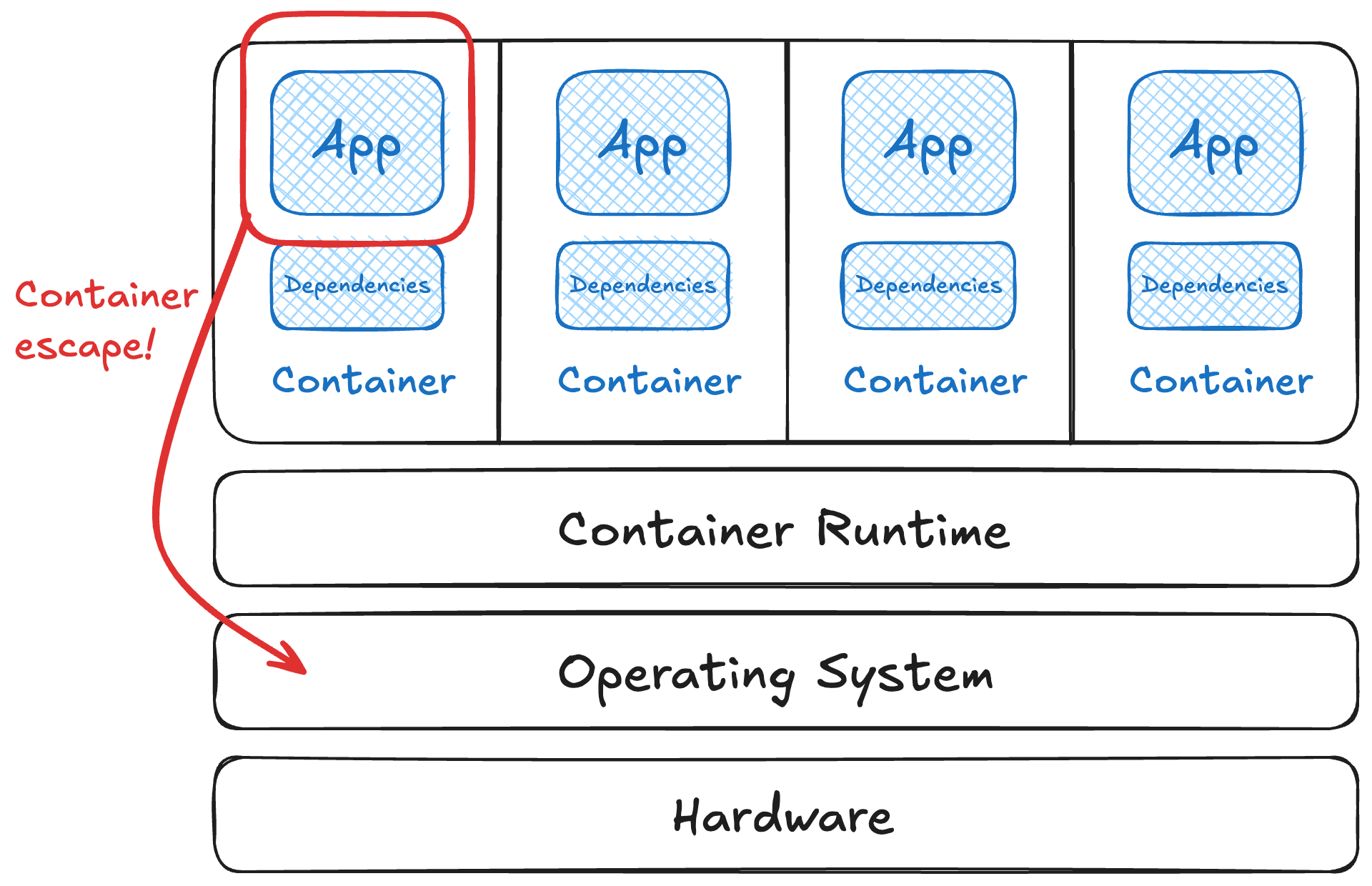
Container Escapes 101
Welcome to Container Escapes 101 at the AppSec Village at DEF CON 33 !!
🎯 Goal: to have a working knowledge of container escapes and how each security measure or risk maps to potential for exploitation. With actual exploits … mostly of misconfigurations or the “rough edges” of containers.
Where we’re going
There’s a lot of hard-earned lessons at the weird intersection of how a no-longer-new technology was designed to operate versus how big organizations actually operate in production. There may still be some novel security research getting done, but it isn’t in this workshop.
Setup
- What’s a container, anyways? - some groundwork on what you’ll need to know
- Setting up our workshop - let’s get our workshop environment set up
Enumeration
- Who am I? - Let’s get oriented and figure out what we have in our container.
- Our shared kernel - Containers are processes that share a kernel. What can we see?
- Are we capable? - What sort of capabilities do we have?
- Seccomp is your friend - Seccomp filters what a container can do. Let’s learn what’s been set for us.
- Are we in a microVM? - With microVM runtimes gaining popularity, how do you know if you’re in a container?
Exploitation
🗺️ Now, let’s map a few paths out of our container.
- Persistent storage - Persisting through persistent storage
- Finding secrets in image layers - Finding secrets in a container image’s layers can be done at runtime if you have access to download it and a shell or access to the host’s socket or access to the registry.
-
Chrooooooooot -
chrootright on out of a container’s filesystem. - Runtime groups - The default “docker” group is basically root.
- Shared runtime sockets - Let’s use a shared socket to create a new container
- Messing with the host’s memory - Let’s modify a process in memory to do fun things!
- Vulnerable apps in the wild - You’re typically not SSH’d into the container host, so … how does this still work in the wild?
🕵🏻♀️ In general, this isn’t a way to gain initial access to a system, but it can be used to move laterally, exfiltrate data, or used with other tactics. Escaping from a container usually isn’t an end in itself.
When you get to the bottom of the page, there are also “previous” and “next” buttons, as well as a block to bring you back here.
All of the workshops have answers hidden as shown below … just click to expand it. There’s no scoring and if you want to just follow along, that’s alright too. We’re all here to learn something. 🌱
Click to see the answer 📚
a secret answer is here!Some things we won’t cover
- Orchestration platforms like Kubernetes, OpenShift, etc. Container escapes are often part of an attack, and orchestrators can be part of that, but they add a bit more complexity than we can cover in 2 hours.
- No novel security research or vulnerabilities - just “bread and butter” container escapes from “holding it wrong”.
- Scripts, enumeration frameworks, Metasploit modules, etc. that go
brrrrrrtand do much of this grunt work for us. We’re keeping it simple to learn manually. These are built on the same fundamentals. 📚 - A lot of new technology that makes some of these escapes harder. From new runtimes (tiny virtual machines), to new runtime enforcement with eBPF , to using more-secure-by-default managed services than what’s economical to run in house - there are plenty of new places to learn and secure our workloads. It changes nothing about needing to understand the basics in order to select, configure, and use these effectively.