Container Escapes 101
Welcome to Container Escapes 101 at the AppSec Village at DEF CON 33!! 🎯 Goal: to have a working knowledge of container escapes and how each security measure or risk maps to potential for exploit...

Welcome to Container Escapes 101 at the AppSec Village at DEF CON 33!! 🎯 Goal: to have a working knowledge of container escapes and how each security measure or risk maps to potential for exploit...
How do you know how much each business unit is using across any number of licensed software or consumably-billed SaaS or compute products? Let’s scope actually doing this having done it before. I...
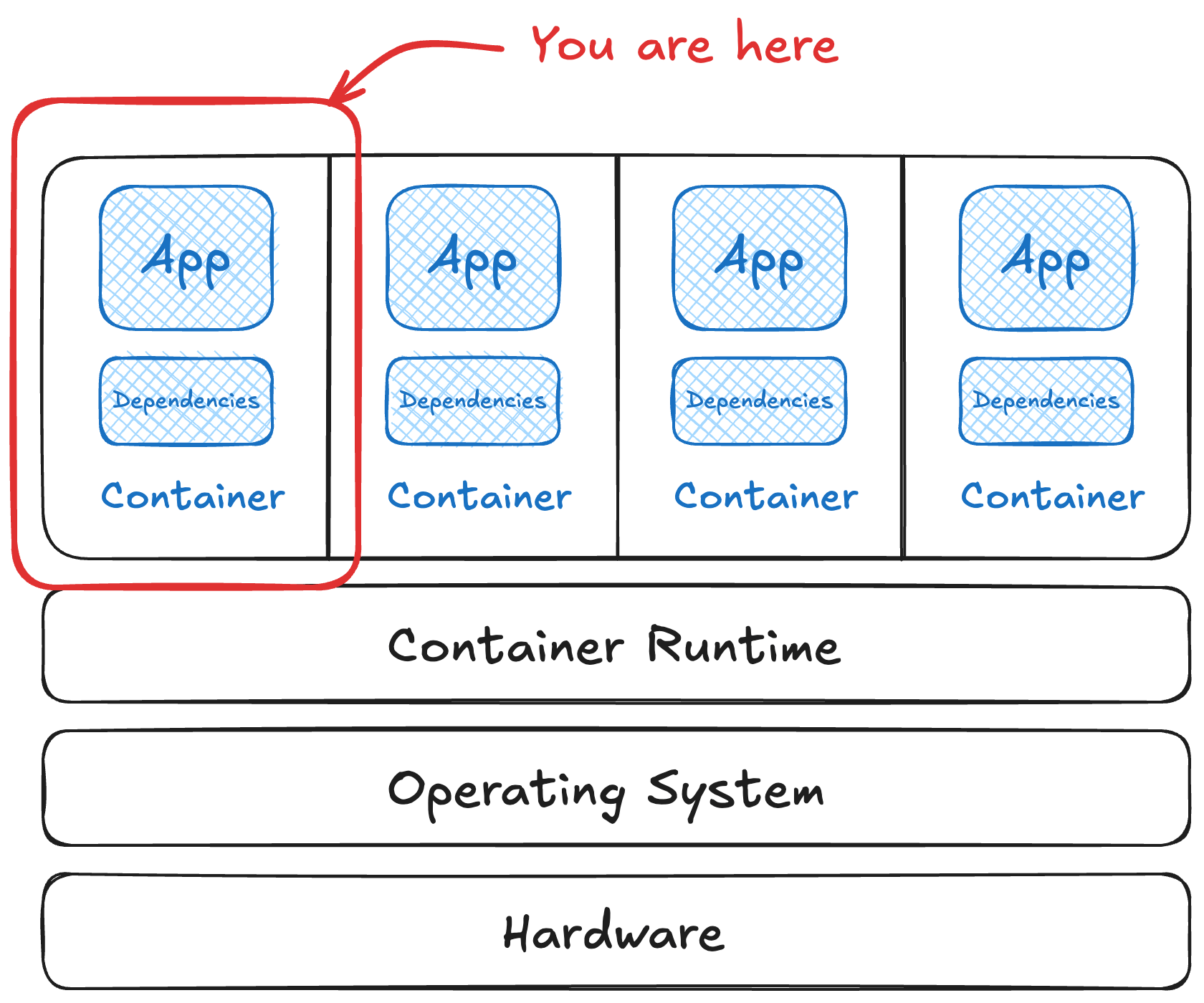
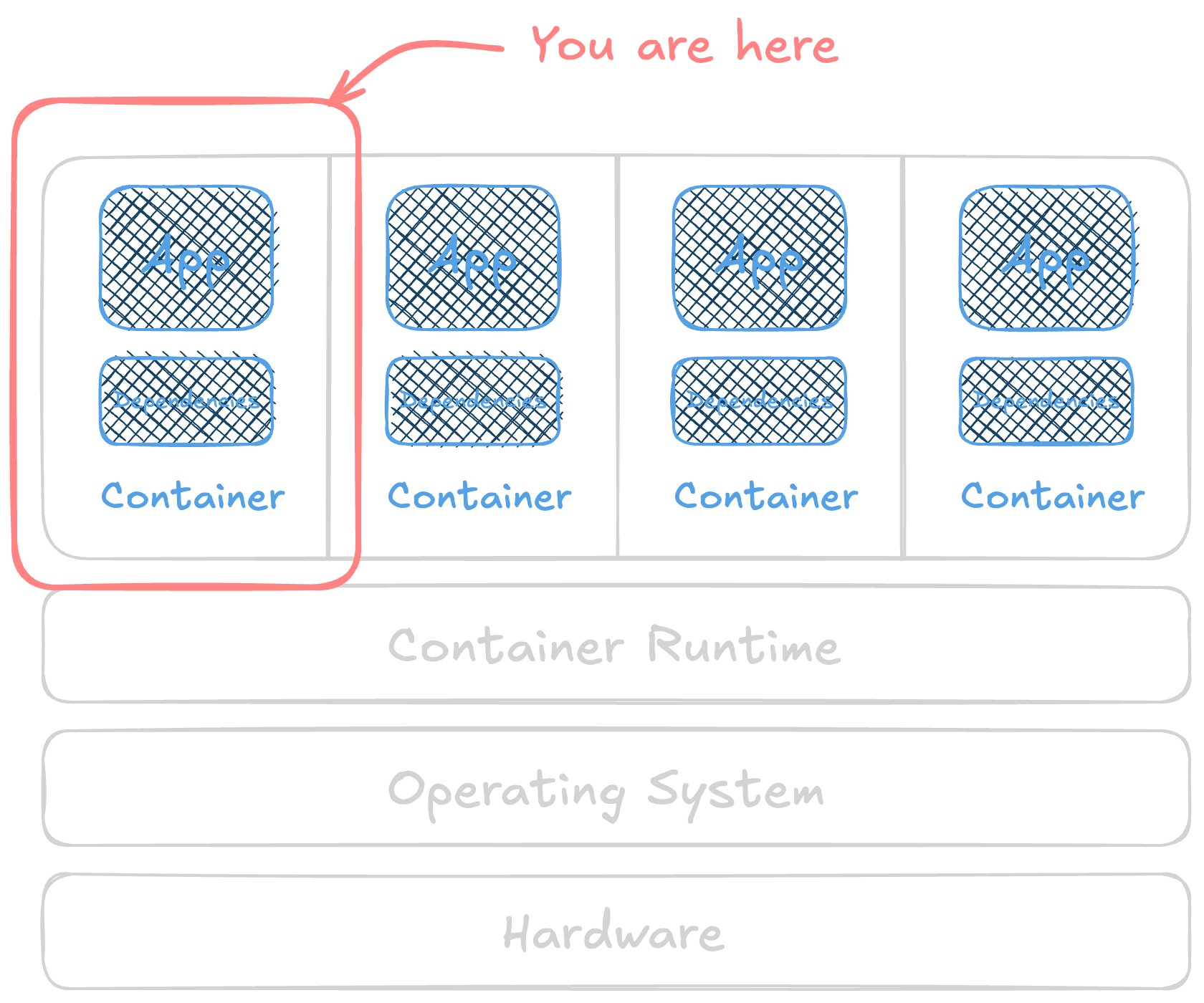
You’ve locked down your runtime, orchestrator, and hosts. Now how about what’s actually running inside of those containers? Container images are too often treated as black boxes until something g...
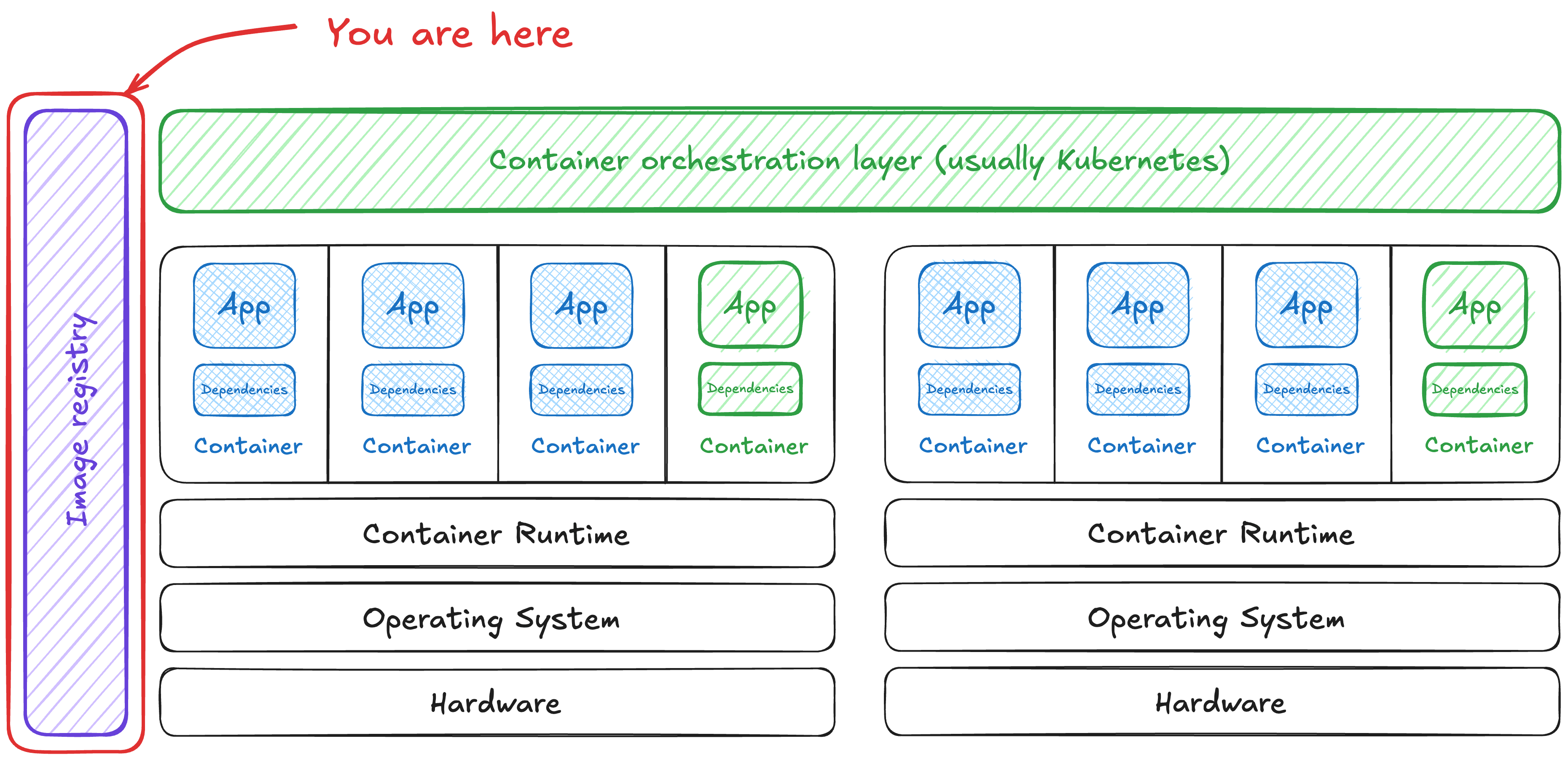
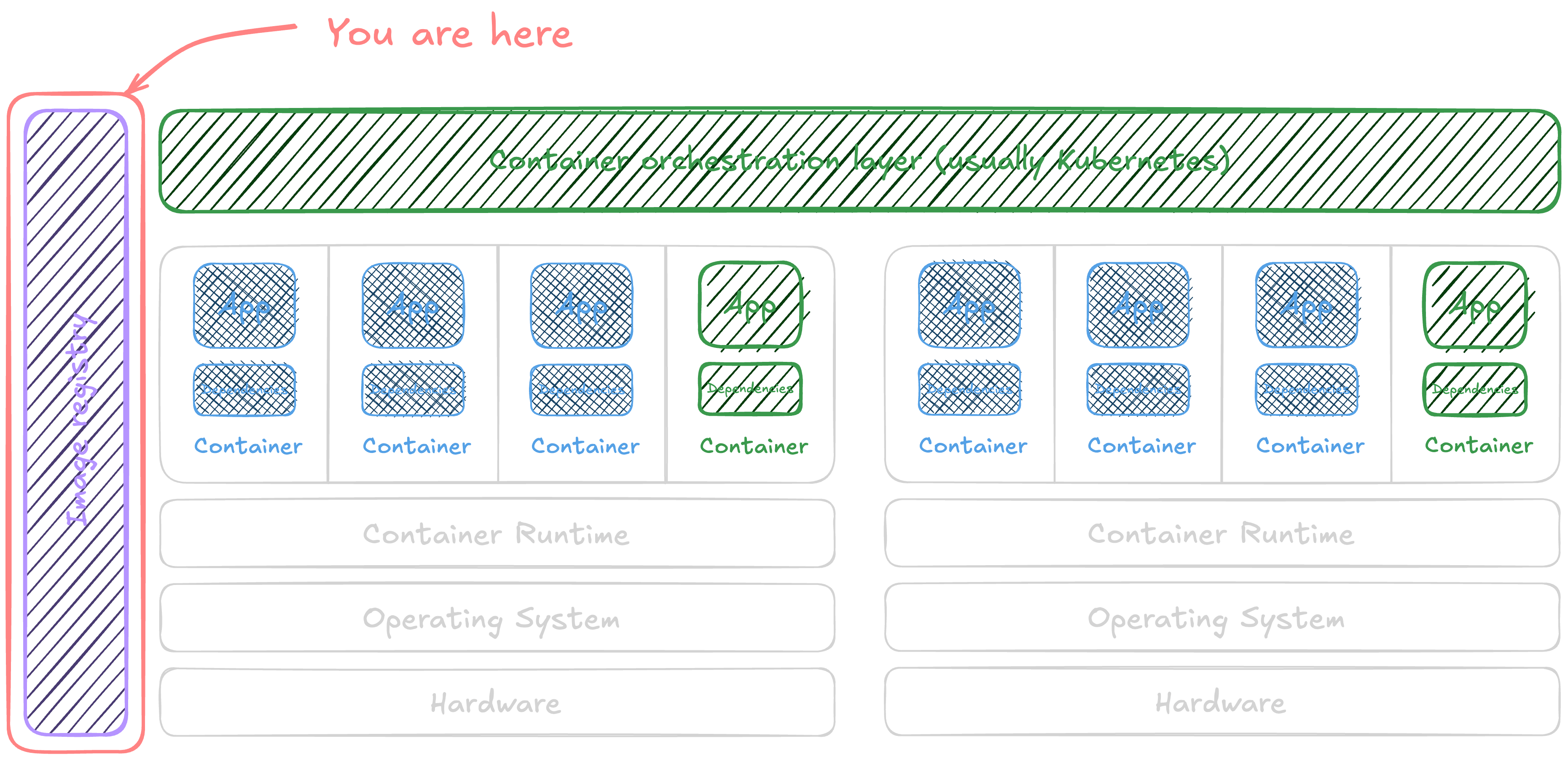
All of these containers are images … somewhere. That ‘somewhere’ is an artifact (or container) registry. What risks can we find in our container registry? Broadly speaking, there are two types o...
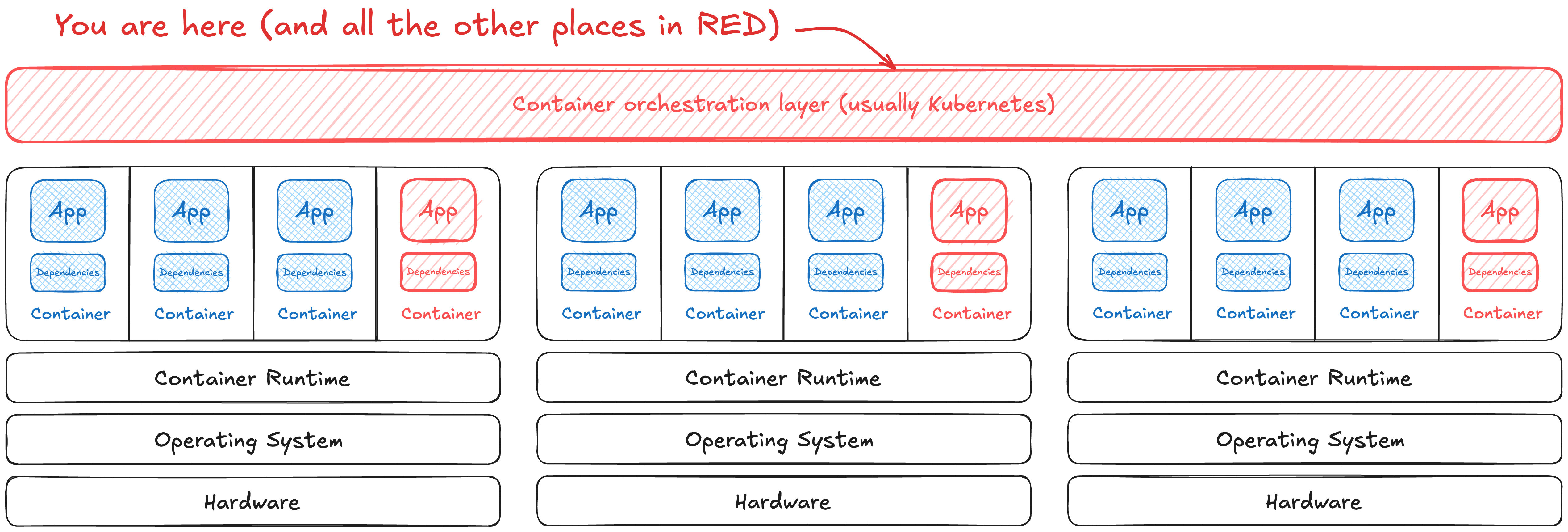
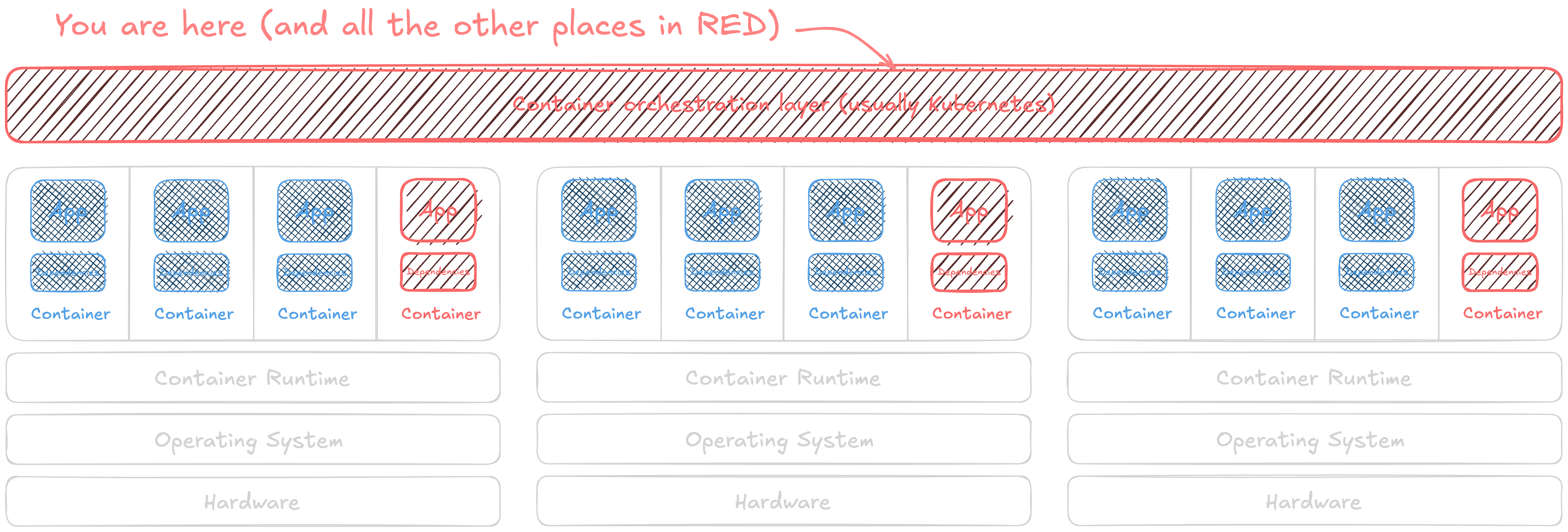
The magic of putting your application in a container is scaling to run even bigger workloads than could fit in a single machine. Container orchestrators have their own risks too. This new layer h...
Let’s walk through how to verify a container image (or any other artifact) signed with Cosign. While open-source software is built in the public, on the internet, it’s still possible to verify sig...
👻 It’s spooky season, so let’s do something a little scary … give AI a bit of power in one of my projects1. I have a chore that’s pure drudgery. It isn’t difficult or fun, just needs to be done m...
It’s been a minute since I’ve done much with custom GitHub Actions runners, but I’ve still been merging Dependabot PRs and otherwise keeping the lights on. While I wrote a few tests, there’s been ...
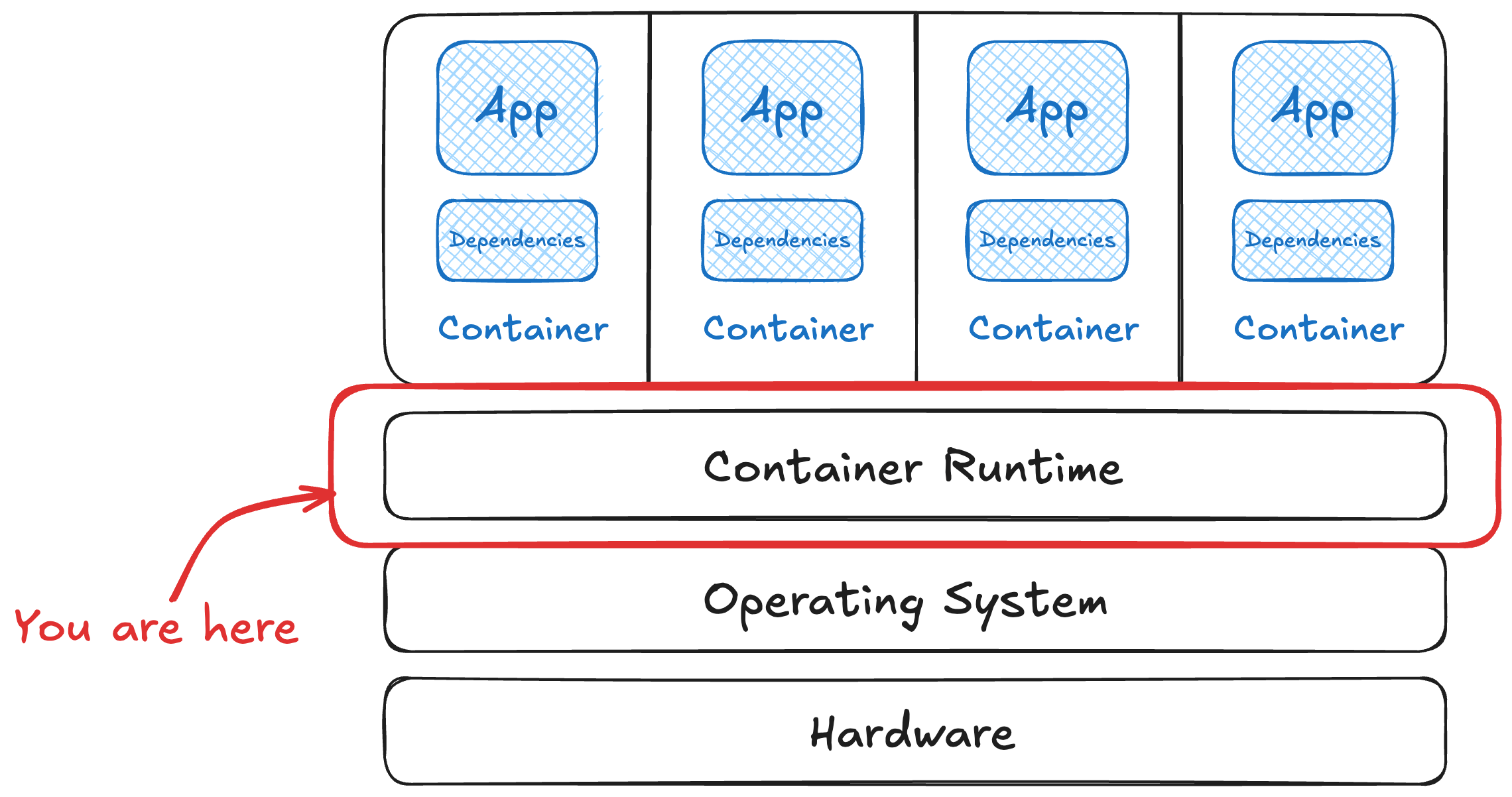
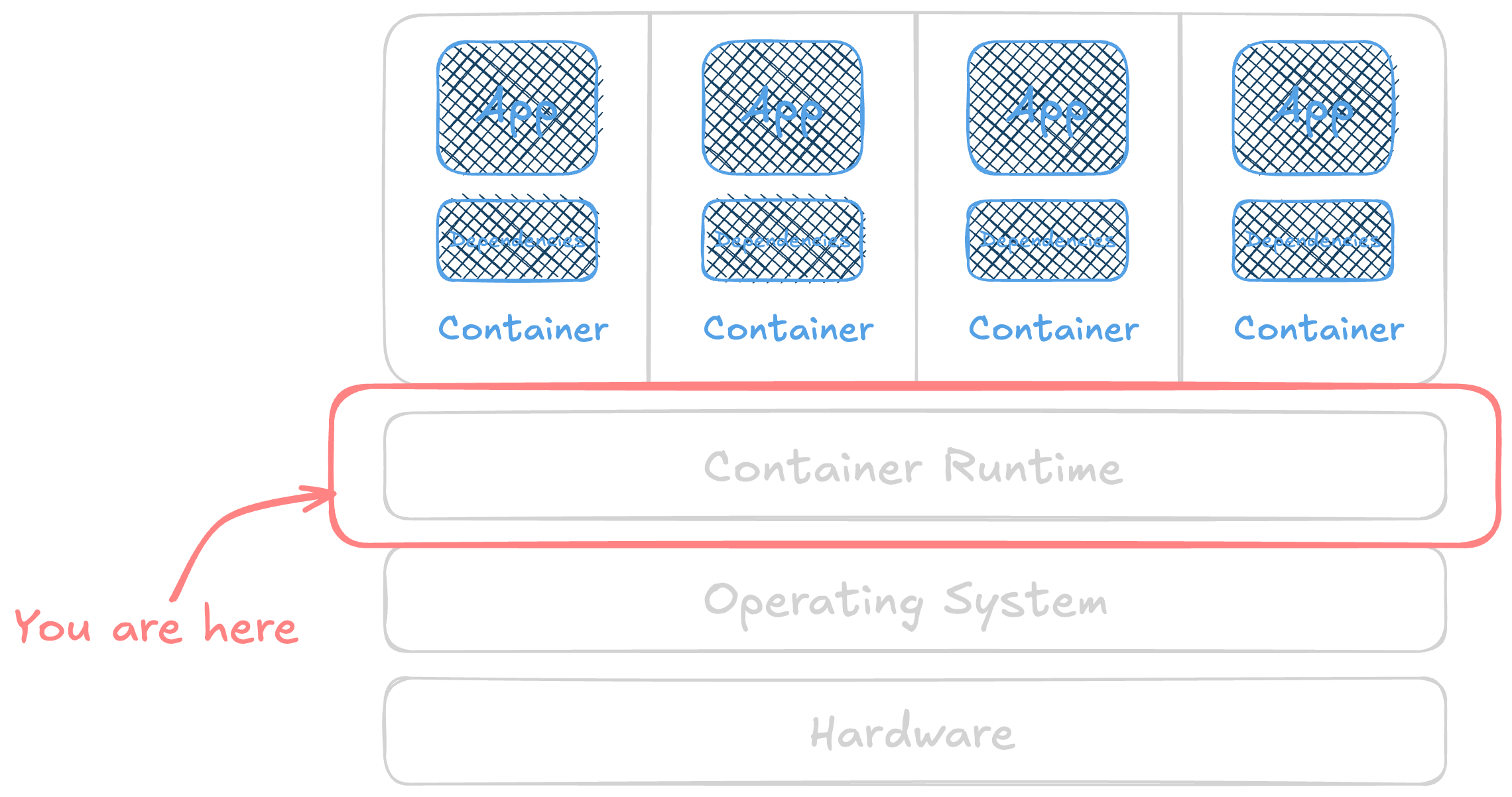
Working our way up the container stack, a runtime is what takes an image and runs it. It also manages its resources, like virtual networking or shared host file system access. A runtime also prov...

A third year of writing on the internet, penning 32 posts for a total of 110 posts. The best part of trying to set a course for the next year is seeing how far I am from both the starting point an...